India major target of ransomware
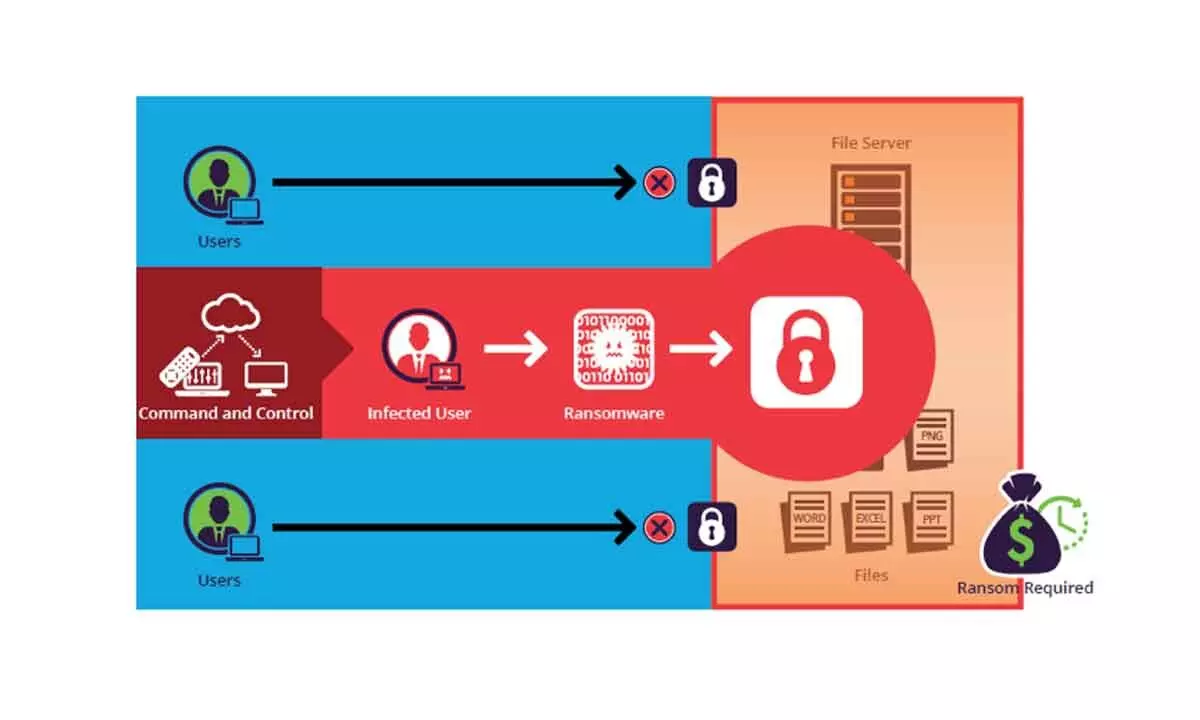
What India needs to prepare for is how to build cyber resilience post a breach. It needs to make sure that the attack time is longer for the hacker, because planting a ransomware doesn’t happen in one day, and then launch the malware. So, the better preventive technologies that it can deploy will reduce the risks
New Delhi: India saw a 53 per cent increase in ransomware incidents in 2022 (year-over-year) and IT and ITeS was the majorly impacted sector followed by finance and manufacturing, India's national cyber agency CERT-In has said in its latest report. Ransomware players targeted critical infrastructure organisations and disrupted critical services in order to pressurise and extract ransom payments in 2022, according to the "India Ransomware Report 2022". "Variant wise, Lockbit was a majorly seen variant in the Indian context followed by Makop and DJVU/Stop ransomware. Many new variants were observed in 2022 such as Vice society, BlueSky etc," said CERT-In.
Last year, a massive ransomware attack disrupted the systems at the All India Institute of Medical Science (AIIMS), crippling its centralised records and other hospital services. According to the CERT-In report, at the large enterprise level, Lockbit, Hive and ALPHV/BlackCat, Black Basta variants became major threats, whereas Conti, which was very active in the year 2021, became extinct in the first half of the year 2022. "Makop and Phobos ransomware families mainly targeted medium and small organisations. At individual level, Djvu/Stop variants continued dominance in attacks over the past few years," the report said. Most of the ransomware groups are exploiting known vulnerabilities for which patches are available.
Some of the product wise vulnerabilities being exploited are in tech companies like Microsoft, Citrix, Fortinet, SonicWall, Sophos, Zoho. and Palo Alto etc, said the report. "Ransomware gangs are commonly using Microsoft Sysinternals utilities such as PsExec for lateral movements," it added.
On an average, the restoration time is about 10 days for infections in reasonably large infrastructure networks. "For smaller networks/infrastructure, the restoration time is around 3 days and for individual systems it is 1 day," the CERT-In report noted. Ransomware gangs are becoming innovative in their approach to improve attack operational efficiency. "Ransomware builders are focusing on speed and performance. Instead encrypting the entire file, a portion of the file is getting targeted for encryption to save time. Multithreading is getting leveraged for faster encryption and decryption of files," the report mentioned.
India experienced approximately 7 lakh malware attacks in 2022, up from 6.5 lakh in 2021, with the banking sector being the most vulnerable to these attacks, totalling 44,949 incidents, a report said. The top six industries affected by malware in India in 2022 were banking, government, manufacturing, technology, healthcare, and finance. However, there was a slight decline in the number of malware detections across the six critical sectors, indicating that appropriate measures are being taken, according to the report by global cyber-security firm Trend Micro.
In 2022, there were a total of 14,983,271 ransomware threats globally, with 38.06 per cent of the attacks targeting Asia, and 10.51 per cent of those attacks being detected in India. "The report reveals a 16 per cent increase in malware attacks, underscoring the need for ongoing vigilance and collaboration to safeguard critical industries such as banking, government, and manufacturing in India," said Vijendra Katiyar, Country manager for India & SAARC, Trend Micro.
In 2021, the top three sectors affected by ransomware were banking, government, and manufacturing, but the trend shifted in 2022 when the Indian government sector became the most affected, followed by manufacturing and banking.
In 2022, Maharashtra was the most-targeted state with 36 per cent of ransomware attacks, while New Delhi was at second, according to the Palo Alto Networks 2023 Unit 42 Ransomware and Extortion report. "Ransomware and extortion groups are forcing their victims into a pressure cooker, with the ultimate goal of increasing their chances of getting paid," said Wendi Whitmore, senior vice president and head of Unit 42 at Palo Alto Networks.
The pace of digitisation has broadened a lot, and hackers now do not differentiate between high-value assets and low-value assets. For them, it's just an asset. They just look at what's the most valuable record. It's no more a credit card or a CVV number, because today we have daily caps on them. So, they are going after patient records, as they are far more valuable than a CVV number, because they offer a patient's health report, his insurance details and his medical history, and there is more value in the underground of a person's health data for marketing and rating points.
Cyberattacks will continue. What India needs to prepare for is how do we build cyber resilience post a breach. It needs to make sure that the attack time is longer for the hacker, because planting a ransomware doesn't happen in one day, and then launch the malware. So, the better preventive technologies that we deploy will reduce the risks.








